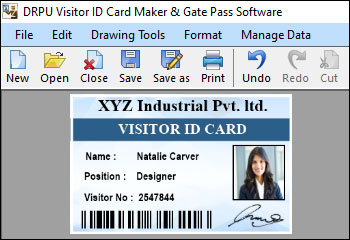
Choose the Right Visitors Management Software for Business
-
Identify your specific
requirements:
Start by understanding your business's unique needs and requirements. Consider factors such as the size of your organization, the number of visitors you typically receive, the level of security required, integration with existing systems (e.g., access control or employee databases), and any specific features you may need.
-
Security features:
Security is a crucial aspect of any Visitors Management Software. Look for features such as photo capture, ID scanning, visitor badge printing, and watchlist screening. These features help enhance security by verifying the identity of visitors, detecting potential threats, and ensuring compliance with safety protocols.
-
Scalability:
Consider whether the software can scale and accommodate your future growth. If you anticipate an increase in the number of visitors or locations, ensure that the software can handle the anticipated volume without compromising performance.
-
Customization and
flexibility:
Assess whether the software allows for customization to align with your branding and specific requirements. Look for options to configure visitor types, badge designs, check-in flows, and fields to capture relevant visitor information.
-
Ease of use:
Look for a user-friendly interface that simplifies the visitor check-in process. The software should be intuitive and easy to navigate for both visitors and staff members. Consider whether it offers features like self-registration or pre-registration options to streamline the check-in process.
-
Reporting and analytics:
Evaluate the reporting and analytics capabilities of the software. The ability to generate reports on visitor statistics, check-in/check-out times, visitor history, and other relevant data can provide valuable insights for security audits, compliance, and operational improvements.
-
Mobile compatibility:
Consider whether the software offers mobile applications or web-based interfaces that allow visitors to pre-register or check-in using their own devices. Mobile compatibility can enhance the visitor experience and reduce waiting times.
-
Reviews and references:
Research and read reviews of the Visitors Management Software you are considering. Look for testimonials or case studies from businesses similar to yours to get an understanding of the software's performance and reliability.
-
Support and training:
Assess the level of support provided by the software vendor. Look for training materials, user guides, and customer support channels such as phone, email, or live chat. Prompt and helpful support can ensure a smooth implementation and address any issues that may arise.
-
Cost considerations:
Evaluate the pricing structure of the software, including any recurring subscription fees, additional charges for features, or implementation costs. Consider your budget and the long-term value provided by the software in terms of improved security, efficiency, and visitor experience.
-
Trial and evaluation:
Whenever possible, take advantage of free trials or demos offered by the software vendors. This allows you to test the software firsthand, evaluate its features, and determine if it meets your requirements before making a final decision.
-
Integration capabilities:
Determine whether the Visitors Management Software can integrate with your existing systems. This can include integration with access control systems, employee databases, email notifications, or other relevant software tools. Integration ensures smooth data flow between different systems, eliminates duplicate data entry, and improves overall efficiency.
Conclusion: By carefully considering these factors and evaluating different Visitors Management Software options, you can select the right solution that aligns with your business needs and helps enhance your visitor management processes.
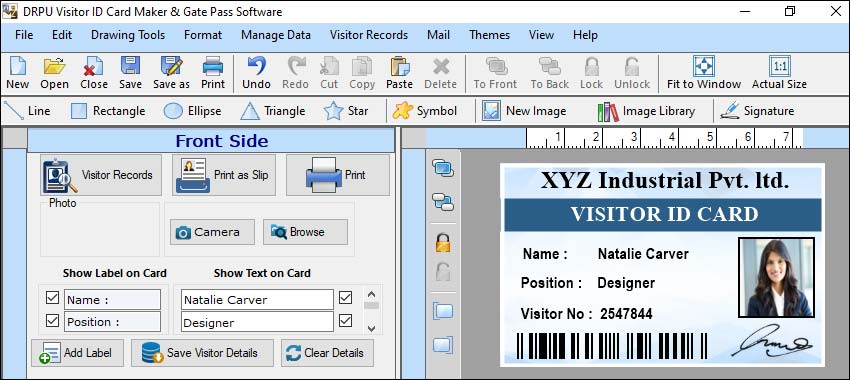
Visitors Management Software can Integrate with other Systems
Visitors Management Software can integrate with other systems like access control and security cameras to enhance the overall security and efficiency of visitor management processes. Here's how these integrations work:
-
Access
Control Integration:
⬗ Visitors Management Software can integrate with your existing access control system to seamlessly manage visitor access to your premises. This integration allows for a streamlined and automated process where visitors can be granted temporary access credentials, such as access cards or temporary badges, during their visit.
⬗ Integration with access control systems enables the Visitors Management Software to communicate with the access control database, automatically create visitor profiles, and grant them access rights based on predefined rules. When a visitor checks in, the system can verify their identity, generate a temporary access credential, and activate it in the access control system. This ensures that visitors only have access to approved areas and for a specific duration, enhancing security and reducing the risk of unauthorized access.
-
Security Camera Integration:
⬘ Integrating Visitors Management Software with security cameras provides an additional layer of security and monitoring capabilities. This integration allows you to capture real-time video or images of visitors during the check-in process and their movements within your premises.
⬘ By linking the Visitors Management Software with security cameras, you can associate visitor information with visual records. This can be useful for security purposes, investigations, or compliance requirements. For example, if an incident occurs, you can easily identify and review the footage associated with a particular visitor or timeframe.
⬘ The integration can also enable features such as live video feeds or video analytics. Live video feeds can be used to monitor the check-in area, allowing security personnel to visually verify the identity of visitors and respond promptly to any issues. Video analytics can provide advanced capabilities such as facial recognition, object detection, or behavior analysis, enhancing the overall security posture of your organization.
-
Other
Integrations:
Besides access control and security cameras, Visitors Management Software can integrate with various other systems and tools to further streamline visitor management processes. Some common integrations include:
⬘ Employee Databases: Integration with employee databases allows for seamless syncing of employee information, making it easier to identify and verify visitors against the list of authorized employees. It ensures that visitors are granted access privileges based on their relationship with employees and predefined rules.
⬘ Email Notifications and Invitations: Integrating with email systems enables the Visitors Management Software to send automated notifications and invitations to visitors. This can include appointment confirmations, parking instructions, or safety guidelines, providing a personalized and efficient visitor experience.
⬘ Watchlist and Security Databases: Integration with watchlist databases allows the Visitors Management Software to perform real-time screening of visitors against watchlists or security databases. This helps identify and flag potential risks or individuals with restricted access, ensuring a higher level of security and compliance.
⬘ Reporting and Analytics Tools: Integration with reporting and analytics tools enables the Visitors Management Software to transfer visitor data for deeper analysis and insights. This integration allows you to generate comprehensive reports, track visitor trends, identify patterns, and make data-driven decisions to optimize visitor management processes.
Conclusion: The specific integration capabilities may vary depending on the Visitors Management Software provider and the compatibility with your existing systems. It's essential to discuss integration requirements with the software vendor and ensure that the necessary APIs (Application Programming Interfaces) or connectors are available to establish seamless communication between the systems.